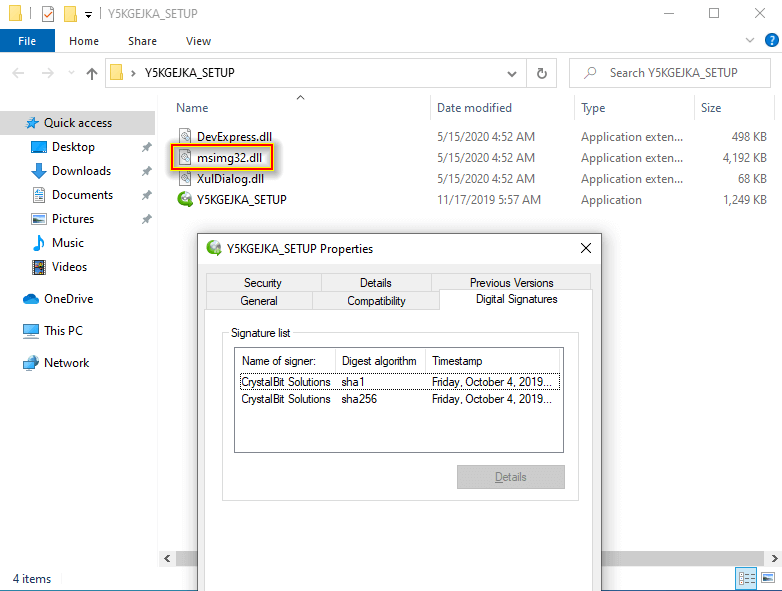
We’ve received two reports from people running Windows who were infected by a Trojan (or some another kind of malware) by executing a file signed by our company (CrystalBit Solutions). More specifically this executable had the AnyToISO icon. How can this be possible?
Unfortunately, it is possible by using a common technique used by cybercriminals called - DLL Search Order Hijacking. In short:
- malware makers use a legitimate executable file signed by a valid digital signature - they simply don’t have their own digital certificate to sign files. In our case they used AnyToISO uninstaller program unins000.exe and renamed it to some random name
- every executable has a list of required Windows system DLL files that must be loaded when this executable starts. In our case msimg32.dll is among them, this Windows library is responsible for Windows graphics device interface (GDI) manipulation
- malware makers put an infected DLL file into the same archive/folder along with legitimate executable. This DLL has the same name (msimg32.dll) as the one from the the required list
- once you run the signed executable Windows looks for required DLL files and gives priority to the local-infected DLL instead of the system one
- infected DLL is loaded into the legitimate process and does its bad things
Bad news is that basically every legitimate and popular app can be abused like that in the Windows world. There’s a known case with TeamViewer, for example.
What did we learn?
- There have never been any infected files in our apps and on the website
- Don’t visit doubtful websites
- Use AntiVirus/Antispyware protection at all times and update it regularly. Windows 10 built-in Windows Defender does its job great
Some technical details:
VirusTotal links for some variants of our signed unins000.exe that were misused by cybercriminals - #1 #2.
VirusTotal links for some variants of infected msimg32.dll - #1 #2.
Demo: